S E R V E R ■ ISDN ■ DSL ■ Fi r e w a l l ■ VPN AVM Access Server Secure Access for Your Network S E R V E R This manual is printed on chlorine-free paper and is therefore completely recyclable.
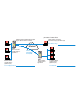
Example The ABC company has its main office in Berlin and a branch location in London. Jane Doe is employed at the main office in Berlin. Because Ms. Doe lives in Hamburg, however, she works from her home. The objective now is to give her a VPN link to the company network, with access to the LAN's mail server. Another VPN link will connect the LANs in Berlin and London.
Jane Doe's home-office Public IP address (dynamically assigned by your Internet Service Provider) Sample address: IP address from address range: 192.168.110.0/24 Your address range: Internet AVM Access Server Sample address: 192.168.10.1 Virtual Private Network (VPN) Berlin office AVM Access Server London office Sample address: 192.168.10.0/24 Sample address: 192.168.20.1 Sample address: 192.168.20.
AVM Access Server This manual and the software it describes are protected by copyright. The manual and software as presented are the object of a license agreement and may be used only in accordance with the license conditions. The licensee bears all risk in regard to hazards and impairments of quality which may arise in connection with the use of this product.
Contents 1 1.1 1.2 1.3 1.4 2 2.1 2.2 3 3.1 3.2 3.3 3.4 3.5 4 4.1 4.2 5 5.1 5.2 5.3 5.4 5.5 5.6 5.7 5.8 5.9 Welcome to the AVM Access Server 6 The AVM Access Server Connects. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6 AVM Access Server Features. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8 Package Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14 System Requirements . . . . . . . . .
6.1 6.2 6.3 6.4 6.5 6.6 6.7 6.8 7 7.1 7.2 7.3 4 AVM Access Server for Experts 100 Architecture of the AVM Access Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100 Internet Access with the AVM Access Server . . . . . . . . . . . . . . . . . . . . . . . . . 102 Connections to Remote Users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 104 Remote Network Connections . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Typographical Conventions The following typographic conventions and symbols are used in this manual to make reading easier and to emphasize important information. Highlighting The table below explains the highlighting conventions used in this manual. Highlighting Function Example Quotation marks Keys, buttons, icons, tabs, menus, commands “Start / Programs”; “Enter” Capital letters Path and file names in running text SOFTWARE\INFO or CAPIPORT.
Welcome to the AVM Access Server 1 Welcome to the AVM Access Server The AVM Access Server seamlessly connects remote users and networks in the company’s communication processes. This means that telecommuters, mobile employees in the field, branch offices and subsidiaries can use the company LAN’s applications and resources from wherever they are. The connection can be a direct ISDN or GSM dial-up link, or a virtual privaten network (VPN) carried over the Internet.
The AVM Access Server Connects The following diagram illustrates the uses of the AVM Access Server: Uses of the AVM Access Server The AVM Access Server interconnects geographically separate networks. In this way central LAN resources, such as servers, mainframes or databases, are available in subsidiary locations and small branch offices as well.
AVM Access Server Features Wide Web, net news, and more. The AVM Access Server also supports the use of web, e-mail and proxy servers, such as AVM KEN! and KEN! DSL. The AVM Access Server interconnects local networks over ISDN based on the open standard PPP over ISDN (Point-to-Point Protocol). This ensures that the AVM Access Server can connect to all ISDN routers that support this standard.
Virtual Private Networks (VPN) Throughput can also be increased by bundling the ISDN B channels– even channels connected to several different ISDN-Controllers. The AVM Access Server in the basic product variant is expandable up to ten channels, thanks to support for up to four AVM ISDN-Controllers B1 or one ISDN-Controller C4 on ISDN BRI (Basic Rate Interface) lines. The PRI (Primary Rate Interface) variant supports the use of up to 120 B channels.
Connection Charge Reduction and Limitation Connection Charge Reduction and Limitation Thanks to intelligent line management, the AVM Access Server ensures that the costs for ISDN connections to remote networks are kept to the bare minimum. The following features minimize costs: The AVM Access Server maintains a logical ISDN connection while interrupting the physical connection.
Security Functions Security Functions The AVM Access Server provides security functions on two different levels. The AVM Access Server incorporates sophisticated features to ensure the authenticity of every site that connects to the LAN over ISDN. Furthermore, data privacy and integrity ensure that no eavesdropping or manipulation of data can take place during transmisssion.
Simple to Install and Configure Remote Site (e.g.
Logs and Use Statistics Logs and Use Statistics Comprehensive statistics and logging abilities permit precise analysis of all events in the router.
Package Contents 1.
Installation and Initial Configuration 2 Installation and Initial Configuration The AVM Access Server is installed by a simple, menu-driven program. When the initial installation is completed, the Configuration Wizard starts automatically and supports you in configuring the basic settings to start the AVM Access Server. We recommend that you plan the basic configuration that you will set up using the Configuration Wizard ahead of time, before you install the AVM Access Server.
Step by Step: AVM Access Server Installation and Basic Configuration Step by Step: AVM Access Server Installation and Basic Configuration The instructions below describe the installation and first configuration steps for the AVM Access Server. The general instructions are accompanied by examples using the settings for the hypothetical scenario.
Step by Step: AVM Access Server Installation and Basic Configuration In the example, the following settings must be entered: 6. In Berlin In London IP address 192.168.10.1 192.168.20.1 Subnet mask 255.255.255.0 255.255.255.0 Default gateway 192.168.10.2 192.168.20.2 If no DNS server address is configured, you must enter addresses of the AVM Access Server’s virtual DNS servers. These addresses are as shown in the example. Preferred DNS server Alternative DNS server 192.168.116.252 192.168.
Step by Step: AVM Access Server Installation and Basic Configuration 5. In the dialog that appears, enter the Product Identification Code that is printed on the back of the CD. 6. In the “Choose Destination Location” dialog, specify the folder in which you want to install the AVM Access Server’s program files. If you are installing the software on a computer running Windows XP, messages about the Windows logo test may appear. Click “Continue Anyway”. 7.
Step by Step: AVM Access Server Installation and Basic Configuration Set up Internet Access In the example, Internet access is set up using ADSL, both in Berlin and in London. 1. In the dialog that follows, specify how the AVM Access Server is to connect to the Internet. In the example, “FRITZ!Card DSL” is selected at both locations 2. Then select the type of Internet Service Provider used. In the example, the option “Internet Service Provider with authentication” is selected 3.
Step by Step: AVM Access Server Installation and Basic Configuration 4. Enter the authentication information for your Internet access account. Create a User Group 1. If you want to provide LAN access to remote users, then specify here how they will be allowed to connect to the AVM Access Server. If you do not want to set up remote users at this time, then deactivate both options.
Step by Step: AVM Access Server Installation and Basic Configuration 3. Select an IP address range. Users in the new group will be assigned IP addresses from this address range. In the example, the IP address range 192.168.110.0/24 is selected Create the First User in the User Group 1. Enter the authentication information for the user. In the “Full name” field, enter the user’s first and last names.
Step by Step: AVM Access Server Installation and Basic Configuration In the example, the option “Activate pre-defined budget” is selected 3. All the settings you have selected are then presented in a summary. Click “Finish” to close the Configuration Wizard. Settings for Unmetered Internet Access If you pay only a flat monthly fee for Internet access, you should activate the AVM Access Server option “Flat rate”. The connection is then maintained continuously, even when idle.
Step by Step: AVM Access Server Installation and Basic Configuration In the example, the following names are entered in the “subdomain name” and “username” fields. For Berlin For London Subdomain name company-abc-berlin company-abc-london Username hqberlin brlondon The fully qualified domain names at which the two AVM Access Servers will later be addressed in the Internet are then “companyabc-berlin.dns4biz.de” and “company-abc-london.dns4biz.de”. 6.
Step by Step on the User’s Home Computer Create an Export File with the Users’ Configuration for NetWAYS/ISDN The AVM Access Server allows you to save the user configuration for an individual remote user in an export file. This file can then be imported in NetWAYS/ISDN on the remote user’s computer. The import operation automatically configures the remote user’s connection to the AVM Access Server. In the example, an export file is created with the user configuration for Jane Doe. 1.
Step by Step on the User’s Home Computer 4. Select the desired Internet Service Provider. 5. Enter a name for your Internet connection. 6. Enter the authentication information for your Internet access account. 7. Click “Next”, then “Finish” to complete the configuration. An icon representing the Internet connection now appears in the NetWAYS/ISDN window. Set up the AVM Access Server as a Remote Network 1. Insert the floppy disk containing the export file created by the AVM Access Server.
Step by Step on the User’s Home Computer 3. On the NetWAYS/ISDN computer, open a command prompt and enter ping followed by the domain name or the IP address of the AVM Access Server. In the example, the command entered on Jane Doe’s NetWAYS/ISDN computer is: ping company-abc-berlin.dns4biz.de If the server’s responses are received, then NetWAYS/ISDN has successfully contacted the AVM Access Server over the Internet. Test Access to a Specific Server in the Company Network from the Remote Workstation 1.
Step by Step: Configuration of the LAN-to-LAN Link Step by Step: Configuration of the LAN-to-LAN Link To configure the LAN-to-LAN link, proceed as follows: Set up a VPN Connection to the Remote Network In the example, the remote network “London Office” is created on the AVM Access Server in Berlin, and the remote network “Berlin Office” is created on the AVM Access Server in London. 1. In the AVM Access Server window, click the “Remote networks” folder with the right mouse button. Select “Add Network...
Step by Step: Configuration of the LAN-to-LAN Link 6. 7. 8. Enter the network address of the local network. In the example, the local network addresses are: In Berlin In London Network address 192.168.10.0 192.168.20.0 Subnet mask 24-255.255.255.0 24-255.255.255.0 Enter the network address of the remote network. In the example, the remote network addresses are: In Berlin In London Network address 192.168.20.0 192.168.10.0 Subnet mask 24-255.255.255.0 24-255.255.255.
Removing the AVM Access Server 2.2 Removing the AVM Access Server 1. Double-click the “Add/Remove Programs” icon in the Windows Control Panel. 2. Select “AVM Access Server” in the list of installed software components. 3. Click the “Change/Remove” button to begin the de-installation procedure. If you want to reinstall the AVM Access Server after removing it, you should first restart the computer after the removal in order to update the entries in the Windows registry.
The AVM Access Server Window 3 The AVM Access Server Window The AVM Access Server window provides all of the configuration and monitoring functions for the AVM Access Server. Once you have installed the AVM Access Server, the Windows Start menu contains the program group “AVM Access Server”. Click the “AVM Access Server” icon in this program group to open the AVM Access Server window. The AVM Access Server window The Access Server window has two different functions: 1.
The AVM Access Server Menus The Access Server window contains the following interactive elements: the menu bar containing the AVM Access Server menus the toolbar, which provides key functions of the AVM Access Server at a mouse-click the Configuration View the Monitoring View the status bar, containing brief information about the operational status of the AVM Access Server 3.1 The AVM Access Server Menus The menu bar provides the commands most frequently used in operating the AVM Access Server.
The ‘Internet’ Menu The ‘Internet’ Menu Menu Command Function Add Internet Service Provider... The “Create New Internet Connection” wizard starts and assists you in configuring the connection to a new Internet Service Provider. Delete Internet Service Provider Deletes the Internet Service Provider currently selected in the object tree. The ‘Remote Users’ Menu Menu Command Function Add User... This command starts a Wizard to aid you in configuring a new user.
The ‘?’ Menu The ‘?’ Menu Menu Command Function Help Topics Opens the AVM Access Server’s Online Help. Manual Opens the AVM Access Server Manual in the Acrobat Reader. Diagnostics Switches the AVM Access Server window to Monitoring View and the selects the “Diagnostics” folder. There you can start a series of diagnostic tests. (See also the section “Diagnostics” on page 43.) Online Registration Opens the online registration page on the AVM web site in your default browser.
Configuration View 3.3 Configuration View The AVM Access Server Configuration View is composed of two parts. The left side of the window shows an object tree, while the right panel shows the properties of the object selected in the tree. Object Tree The AVM Access Server object tree has the following structure: Object tree in the Configuration View The AVM Access Server groups configuration objects in the predefined folders “Internet”, “Remote users”, “Remote networks”, “Security”, and “Administration”.
Object Properties Object Properties The right panel in the Access Server window displays the properties, or settings, of the object or folder selected in the tree in the left panel. The properties display can contain one or more dialog pages, depending on the folder or object selected. The configuration settings can be edited on these dialog pages.
Monitoring View 3.4 Monitoring View The Monitoring View provides connection control, monitoring and diagnostics functions. Like the Configuration View, the Monitoring View is also composed of two parts. The monitoring functions are shown in the tree display on the left. The object tree in Monitoring View The display panel on the right contains one or more dialog pages, depending on the function selected in the object tree in the left panel.
AVM Access Server Monitor AVM Access Server Monitor Select “AVM Access Server Monitor” in the object tree to display information about the installed product version and a brief summary of the AVM Access Server’s momentary status. Connection Control The “Connection Control” page lists the AVM Access Server’s ISDN, ADSL and VPN connections with their momentary status. Commands are also provided to trigger various actions, depending on the connection status.
Connection Control Icon Status ADSL outgoing One B channel outgoing One B channel incoming Two B channels outgoing Two B channels incoming VPN outgoing There is a logical and physical connection to the remote user or network. In other words, the ISDN B channel or the ADSL channel is connected, and connection charges are accumulating. The direction of the arrow illustrates the direction of the connection request.
ISDN B Channels Properties Click a connection in the list with the right mouse button and select “Properties” in the context menu to display the IP address assignment, compression and filtering options, and the security associations (SAs) of VPN connections. For a detailed description of the properties, see the Online Help. ISDN B Channels Select “ISDN B channels” to display all of the ISDN connections that are currently active.
Events Events Events displayed in the Monitoring View include all ISDN, ADSL, and VPN operations, as well as error and informational messages. These events are divided into categories indicated by different icons. The messages types are: Icon Event type Warning, such as a user budget or global threshold that has been exceeded. Informational message, such as a successful connection setup or clear-down.
Packet Trace The following information is supplied for all connections established between the AVM Access Server and the remote site, broken down by user and network: the total number of connections the number of direct dial-in connections the number of VPN connections the number of incoming connections the number of outgoing connections the total connection up-time the total up-time of all direct dial-in connections the total up-time of all VPN connections the total traffic volume Connections that are stil
Packet Trace The following instructions describe how to generate a packet trace based on two typical examples. Packet Trace for Negotiation Diagnostics 1. Select the “Packet trace” folder. 2. Select the following options on the “Settings” dialog page: Option Setting Interface (Ethernet, PPP, PPPoE) Activate User or network Activate and select the desired user or network Interface Activate and select the desired interface 3. Use the default settings for the buffer and packet size. 4.
Diagnostics 4. Wait until 20 to 100 packets have been captured, then stop the packet trace by clicking the “Stop” button. 5. Save the results of the packet trace in a file for further analysis. For further details on the Packet Trace function, please see the Online Help. Diagnostics The “Diagnostics” folder provides a diagnostic tool that allows you to test all the components that are important for the AVM Access Server in just a few seconds.
AVM Access Server Use Scenarios 4 AVM Access Server Use Scenarios This chapter describes the use of the AVM Access Server in various configurations and application scenarios. The installation and configuration of the AVM Access Server is described in detail for each scenario, with special attention to points that are important for you to note. 4.1 LAN-to-LAN Link Using AVM ISDN-Controller C4 and Eight B Channels A company has its main office in Berlin and a subsidiary in London.
Technical Requirements The following illustration shows a diagram of the LAN-to-LAN connection. Berlin main office London office IP address: 192.168.10.0 Subnet mask: 255.255.255.0 IP address: 192.168.20.0 Subnet mask: 255.255.255.
Task Checklist Task Checklist The following steps must be carried out both in the main office in Berlin and at the London subsidiary: Installation and configuration A Verify the network settings in the Windows Control Panel B Install the AVM Access Server C Configure the ISDN-Controller for the appropriate line type D Create a remote network in the AVM Access Server with channel bundling for a total of eight B channels E Create a schedule and activate it in the remote network configuration F Tes
Step by Step 4. Enter the following settings at the two locations: In Berlin In London IP address 192.168.10.1 192.168.20.1 Subnet mask 255.255.255.0 255.255.255.0 Default gateway 192.168.10.2 192.168.20.2 The default gateway entry can be any IP address in the AVM Access Server’s subnetwork. B 5. Confirm by clicking “OK”. 6. If want to use any other additional LAN adapters with the AVM Access Server, you must enter a fixed IP address for each such adapter as described above.
Step by Step D 6. In the “Budget settings” dialog, select the option “Start with no pre-defined budget”. 7. Click “Finish” to close the Configuration Wizard. Create a Remote Network in the AVM Access Server with Channel Bundling for a Total of Eight B Channels The remote network “London Office” must be set up on the AVM Access Server in Berlin, and the remote network “Berlin Office” must be set up on the AVM Access Server in London. 1.
Step by Step E Create a Schedule and Activate it in the Remote Network Configuration In order to allow use of the connection only during business hours, from Monday through Friday between 9:00 a.m. and 5:00 p.m., you must define a schedule and activate it in the settings for the remote network. 1. Click with the right mouse button on the folder “Administration / Schedules”, and select “Add Schedule...” in the context menu. 2. On the “General” dialog page, enter a name for the schedule. 3.
AVM Access Server and a Router 4.2 AVM Access Server and a Router A translation agency with ten employees uses a dedicated router to provide Internet access for all the workstations in the LAN. Now the AVM Access Server and NetWAYS/ISDN will be added to permit all employees to access the company’s e-mail server from home. The employees will access the company LAN from their home offices over VPN links. The router will continue to provide Internet access.
Technical Requirements Technical Requirements In the translation agency office – a computer in working order which fulfills the system requirements for the AVM Access Server – a leased-line connection to the Internet (2 Mbit/s) – Internet access through a router connected to the leased line – a Lotus Domino e-mail server In the employees’ home offices: – a computer in working order – FRITZ!Card PCI – an ISDN line with unmetered access – an account with an Internet Service Provider Task Checklist In the tr
Step by Step: On the Server in the Translation Agency Office In the employees’ home offices: Installation and configuration A Install NetWAYS/ISDN (included in the AVM Access Server package) B Configure the connection to the Internet Service Provider C Configure the AVM Access Server as a remote VPN network D Test the Internet connection E Test the VPN connection from the home PC to the AVM Access Server F Test access to the e-mail server from the home computer Step by Step: On the Server in the
Step by Step: On the Server in the Translation Agency Office B 4. In the “IP address” field, enter a fixed, public IP address. This IP address must be in the IP subnetwork assigned to your leased line by the service provider. 5. If no DNS server address is configured, you must enter addresses of the leased-line provider’s DNS servers. 6. Confirm your choices by clicking “OK”. 7.
Step by Step: On the Server in the Translation Agency Office D Test the Accessibility of the AVM Access Server from the Internet In order for the remote users to establish VPN connections to the AVM Access Server, the AVM Access Server must be accessible at a known address in the Internet. E F 1. Select the “Internet” folder in the object tree in the AVM Access Server window. 2.
Step by Step: On the Server in the Translation Agency Office G Create Export Files with the Users’ Settings for NetWAYS/ISDN The AVM Access Server allows you to save the user settings for individual remote users in an export file. This file can then be imported in NetWAYS/ISDN on the remote user’s home computer. The import operation automatically configures the remote user’s connection to the AVM Access Server. Carry out the following steps for each employee individually. 1.
Step by Step: On the Employees’ Home Computers Step by Step: On the Employees’ Home Computers Steps A through F described below must be carried out on each employee’s home computer. A Install NetWAYS/ISDN (Included in the AVM Access Server Package) Install NetWAYS/ISDN according to the instructions in the NetWAYS/ISDN manual. B Configure the Connection to the Internet Service Provider T-Online 1. In the “Settings” menu, select “Call destinations / New call destination...”.
Step by Step: On the Employees’ Home Computers D Test the Internet Connection You can test the Internet connection by sending a “ping” to any server in the Internet. 1. The NetWAYS/ISDN Internet connection must be on stand-by. In the NetWAYS/ISDN window, select the Internet connection, then click “Standby to connect” in the “File” menu. 2. Open a command prompt and enter ping www.avm.de. If the server’s responses are received, then NetWAYS/ISDN has successfully established a connection to the Internet.
AVM Access Server Concepts and Functional Principles 5 AVM Access Server Concepts and Functional Principles This chapter presents a number of the features and options provided by the AVM Access Server. Settings are described with their underlying concepts, areas of application, and actual functions in the AVM Access Server as a whole. 5.
Filters and Rules Because the filter rules are grouped in several instances, they provide very flexible and extensive control. The packet filtering performed by the AVM Access Server is one way of setting up what is called a firewall, a protective barrier around your network.
Filters and Rules Rules consist of the following components: A description of the packet type to which the rule applies. The AVM Access Server tests packets against the descriptions in the filter rules by three criteria. – Service: The rule may apply to all IP-based services, or only to certain services such as FTP or telnet, or just to specific service operations, such as FTP access to the LAN from the Internet. – Source of the packet: this is specified in the form of a network or host address.
Filters and Rules When creating a filter, you should bear these two important points in mind: Each filter profile always treats all packets: the specific rules apply to certain packets; the default action applies to all others. The order of the rules in the list is important! You must always make sure that rules with more specific packet descriptions are placed higher in the list than more general rules.
Examples of IP Filter Profiles The diagram below illustrates the order in which packets traverse the AVM Access Servers filters.
Examples of IP Filter Profiles The profiles “Incoming Internet profile (upper, stateful)” and “Incoming Internet profile (lower, stateful)” should be used only if IP masquerading is not activated. The “Outgoing Internet filter profile” can be used in any case. You can also customize the filter profiles to suit your needs. In filtering services, you can also distinguish between inbound and outbound connection set-up by matching the flags in the TCP header.
Examples of IP Filter Profiles Incoming Internet Profile (Lower Only) “Incoming Internet profile (lower only)” Profile active Yes Name Incoming Internet profile (lower only) Default action Drop Rules Status 64 Service/Source/Destination Action Remarks Inactive HTTP connection set-up Accept (Hypertext Transfer Protocol) Activate this rule if you want to allow access to a local web server.
Examples of IP Filter Profiles Status Service/Source/Destination Action Remarks Inactive NTP packets (Network Time Protocol) Accept Activate this rule if you operate an NTP time server in your LAN and want it to be accessible from the Internet. Inactive UUCP connection set-up Accept Activate this rule if your Internet Service Provider sends you data, such as news or mail, by UUCP.
Examples of IP Filter Profiles 66 Status Service/Source/Destination Action Remarks Active FTP data connection set-up (File Transfer Protocol) Accept This ensures that your local users can download files from FTP servers in the Internet. Note: You can deactivate this filter rule if all FTP clients in your network use “passive FTP”. Active TCP connection set-up Drop This rule discards all attempts to set up TCP connections, except those explicitly accepted by one of the active rules listed above.
Examples of IP Filter Profiles Status Service/Source/Destination Action Remarks Inactive GRE packets (Generic Routing Encapsulation) Accept Activate this rule if you are using GRE-based tunneling mechanisms in your LAN, such as the PPTP VPN gateway incorporated in Microsoft NT 4.0. This rule is not necessary if you are only using the AVM Access Server’s VPN functions. Active Drop All packets that have not been accepted or dropped above this point are treated as intrusion attempts.
Examples of IP Filter Profiles Outgoing Internet Filter Profile “Outgoing Internet filter profile” Profile active Yes Name Outgoing Internet filter profile Default action Accept Rules 68 Status Service/Source/Destination Action Remarks Active ESP packets (Virtual Private Network) Accept If you have configured VPN connections, activate this rule for the Internet connection over which the VPN links are carried.
Examples of IP Filter Profiles Incoming Filter Profile (Upper, Stateful) “Incoming Internet profile (upper, stateful)” Profile active Yes Name Incoming Internet profile (upper, stateful) Default action Drop Rules Status Service/Source/Destination Action Remarks Active All packets for outgoing connections Accept This rule is part of the AVM Access Server’s “stateful” packet inspection. Do not change this rule if you want to use stateful inspection.
Examples of IP Filter Profiles Incoming Internet Profile (Lower, Stateful) “Incoming Internet profile (lower, stateful)” Profile active Yes Name Incoming Internet profile (lower, stateful) Default action Drop Rules Status Service/Source/Destination Action Remarks Active All packets for outgoing connections Accept This rule is part of the AVM Access Server’s “stateful” packet inspection. Do not change this rule if you want to use stateful inspection.
Examples of IP Filter Profiles Status Service/Source/Destination Action Remarks Inactive HTTP connection set-up Accept (Hypertext Transfer Protocol) Activate this rule if you want to allow access to a local web server. Inactive FTP connection set-up (File Transfer Protocol) Accept Activate this rule if you want to allow access to a local FTP server.
Examples of IP Filter Profiles Status 72 Service/Source/Destination Action Remarks Inactive Telnet connection set-up Accept Activate this rule if you want to allow Telnet access to your computers (for remote administration of UNIX computers, for example). Inactive SSH connection set-up Accept Activate this rule if you want to allow SSH (Secure Shell) access to your computers (for remote administration of UNIX computers, for example).
Examples of IP Filter Profiles VPN Packets Only (Lower) This pre-configured profile can be used to prevent the Access Server from establishing any connections with computers in the Internet except VPN connections.
IP Masquerading and Forwarding Profiles Status Service/Source/Destination Action Remarks Active All packets All packets that have not been accepted or dropped above this point are treated as intrusion attempts. These may be tunnelled packets (i.e. IP-over-IP encapsulated packets), or routing protocols, such as OSPF or EGP packets. These packets would also be dropped by the filter profile’s default action, of course.
Forwarding Profiles communicating with Internet hosts. Because only requested data is forwarded into the LAN, the private LAN is protected against unauthorized access from the Internet. The AVM Access Server’s use of IP masquerading provides the following advantages: Each time the connection to the Internet Service Provider is reestablished after an inactivity timeout, the Access Server is assigned a new IP address.
Forwarding Profiles The rules in the forwarding profiles are listed with explanations in the tables below. Forwarding Profile “Gateway Services” Profile active Name Yes Gateway Services Rules Status 76 Service/Source/Dest Protocols ination Remarks Inactive FTP/ 0.0.0.0 : 21/ 0.0.0.0 : 21 TCP Activate this rule if you have an FTP server in your localarea network and want to make it accessible from the Internet. Inactive SSH/ 0.0.0.0 : 22/ 0.0.0.
Static and Dynamic Routing Status Service/Source/Dest Protocols ination Remarks Inactive HTTPS/ 0.0.0.0 : 443/ 0.0.0.0 : 443 TCP Activate this rule if you have an HTTPS server (i.e. a secure web server) in your local-area network and want to make it accessible from the Internet. Inactive ISAKMP (VPN)/ 0.0.0.0 : 500/ 0.0.0.0 : 500 UDP If you have configured VPN connections, activate this rule for the Internet connection over which the VPN links are carried. Inactive AVM Web Server/ 0.0.0.
Reserving B Channels Static routing All information about destination networks and the paths by which they can be reached is configured manually, and changed only by the administrator. Dynamic routing All routers in the network can exchange information about subnetworks and the paths to them by means of a routing protocol. Routers regularly update their own routing tables automatically based on the information received.
Restricting Access to Scheduled Times The system administrator must ensure that enough B channels are always available if most of the remote sites have been configured to maintain logical ISDN connections (i.e., their disconnect timeout under “End idle logical connection” is set to “Later than Inactivity Timeout” or “Never”).
Cost Assignment (COSO, Charge One Site Only) 5.6 Cost Assignment (COSO, Charge One Site Only) The ISDN feature “D channel signaling” is provided free of charge by most ISDN operators, and is used by the AVM Access Server to implement cost allocation (COSO, Charge One Site Only). COSO allows you to specify which end of the network link bears the connection charges. For each remote network user group, this may be the local ISDN Access Server, or the remote site, or whichever site initiates the connection.
Virtual Private Network (VPN) 5.7 Virtual Private Network (VPN) The AVM Access Server allows you to set up Virtual Private Network (VPN) connections. VPN connections are an economical way to connect both remote networks and single remote PCs to the company LAN. Until recently, remote systems were usually interconnected using direct dial-up or leased line connections over public telecommunication networks, such as ISDN or GSM.
VPNs in the AVM Access Server VPNs in the AVM Access Server The term VPN refers simply to a private link carried over a public infrastructure. Which mechanisms are used to accomplish this is not specified. The AVM Access Server sets up its VPN links over existing Internet connections, taking advantage of the Internet Service Provider’s infrastructure. The Internet Service Provider has nothing to do with the actual VPN connections, however, nor with the network communication between the systems involved.
Security right mouse button and select “Add Group...” in the context menu to start the Wizard that supports you in configuring the VPN connection settings for a new user group. In the process you will specify whether the users in the group are authorized to connect over VPN links. When you select a user group in the “Remote users” folder, the settings for the group are shown on a number of dialog pages in the properties display. The settings can be edited on these dialog pages.
The VPN Protocol IPsec IPsec is a network-layer (ISO OSI Layer 3) protocol, and hence independent of the underlying infrastructures. However, IPsec is limited to the IP network protocol. In other words, only IP can be transported over an IPsec-based VPN. IPsec permits two different operating modes: Tunnel Mode and Transport Mode. Transport Mode does not create a tunnel, and strictly speaking does not provide a virtual private network. Only Tunnel Mode is used in VPN connections.
The VPN Protocol IPsec The IP addresses in the example above are used in different ways: Local Network – The local network has the network address 192.168.10.0/24. – Each client computer in the local network has an IP address in the address range defined by this network address. These are all private IP addresses which must never appear in the public Internet. They are reserved under RFC 1918 for communication within private LANs.
The VPN Protocol IPsec In the encapsulated packets transported over the IPsec tunnel between the two AVM Access Servers, different IP addresses appear in the original packet's IP header and in the encapsulating packet header: IP addresses in the original packet Destination The private IP address of the computer in the local network that is the intended recipient of the communication.
The IPsec Transport Protocols Remote Networks In configuring a VPN connection, you must indicate the IP network addresses of the local and remote networks. The Wizard then automatically generates an access rule in the AVM Access Server which specifies that packets with a source IP address in the local network and a destination in the remote network are transported with IPsec encapsulation.
The IPsec Transport Protocols Prevents replay and detects man-in-the-middle attacks: AH contains a unique serial number that can be used to identify packets replayed by a third party. AH does not provide encryption of the data payload. The diagram below illustrates the original packet and the IPsec encapsulated packet with AH.
Negotiation Negotiation Many combinations of encryption and authentication parameters are possible in VPN connections. When establishing a secure VPN connection, the communicating parties must agree on the parameters they want to use. Negotiation of the connection parameters requires another protocol, called Internet Key Exchange (IKE). The agreed parameters determined by IKE negotiation are stored in a Security Association (SA).
Negotiation IKE Phase 1 The purpose of IKE Phase 1 is to negotiate an SA to provide secure communication during IKE Phase 2. In IKE Phase 1, the two peer systems perform the following steps: They communicate their identities. They authenticate themselves. They negotiate an encryption algorithm to be used in IKE Phase 2. They negotiate a Diffie-Hellman group to use in generating keys. Each system generates a private key, and generates a corresponding public key using the negotiated Diffie-Hellman group.
Authentication Using Certificates IKE Phase 2 The goal of IKE Phase 2 is to negotiate the SAs for the encryption of actual user data. This negotiation is itself encrypted based on the SA that was negotiated in Phase 1. The following parameters are negotiated: the IPsec transport protocol (AH and/or ESP) the encryption algorithm for user data transmitted over the VPN connection The AVM Access Server provides the encryption algorithms DES, 3DES and AES for this purpose.
Authentication Using Certificates Asymmetrical Encryption Techniques Asymmetrical or “public key” encryption techniques do not use the same key for encryption and decryption. Rather, a pair of keys is required with the following properties: Neither key can be reconstructed from the other. Either key can be used for encryption, but a string encrypted with one key can only be decrypted with the other key. One key is made publicly available, while the other is kept strictly secret.
Authentication Using Certificates When a certificate is issued, a key pair is generated consisting of a public and a private key. The public key is a component of the certificate, while the private key is given to the applicant alongside the certificate in the PKCS#12 file. The AVM Access Server manages all the certificates issued by its certification authorities, along with their key pairs, in an internal list. Each certification authority’s certificates are listed on its “Certificates Issued” dialog page.
Compression Techniques (IPComp) In this case, the digital signature is considered to be valid. A certificate is valid if the following conditions are met: The certificate was issued by a certification authority that the AVM Access Server trusts. In other words, the certification authority’s root certificate must be present in the AVM Access Server. The certification authority’s digital signature must be valid. The AVM Access Server can verify this using the certification authority’s root certificate.
Dynamic DNS 5.8 Dynamic DNS Dynamic DNS is an Internet service that allows the AVM Access Server to be continuously identifiable by a constant domain name even when it does not have a constant public IP address. Dynamic DNS is offered by both free and commercial providers. The AVM Access Server supports two dynamic DNS providers, “Dynamic DNS Network Services” and “companity, Andreas Wilkens”.
Windows Name Resolution with the AVM Access Server NetBIOS names are easier for users to work with than the purely numeric IP addresses. In order for NetBIOS services to be transported over the network, however, the NetBIOS names must be mapped to IP addresses. A number of mechanisms serve this purpose. In a Windows LAN, NetBIOS names are resolved automatically. This takes place by means of name information which all Windows computers in the network broadcast to one another.
Windows Name Resolution with the AVM Access Server Name Resolution Methods In addition to deactivating the NetBIOS filter, you should set up a suitable method of NetBIOS name resolution in the Windows network. Possible methods are listed here only as a first hint. Please see the Online Help in your Microsoft operating system and www.microsoft.com for detailed instructions. NetBIOS name resolution can be performed statically or dynamically.
Windows Name Resolution with the AVM Access Server Dynamic Name Resolution using WINS The static LMHOSTS file is not practical in networks in which computers’ IP addresses or names change frequently (due to dynamic IP address assignment by DHCP, for example). For such cases Microsoft has developed the Windows Internet Naming Service (WINS). WINS is an integral part of Windows NT and 2000 servers, and can be installed as an additional network component.
Note on the Microsoft Browsing Service WINS over LAN-to-LAN links In order to use WINS name resolution over a remote network connection, a WINS server must be used in each of the two networks. WINS includes replication functions that allow the two WINS servers to collate their databases at regular intervals, so that name resolution can take place across the subnet boundary.
AVM Access Server for Experts 6 AVM Access Server for Experts This chapter is a compact technical summary of the AVM Access Server’s architecture and functions, and is intended only for networking experts. It is aimed at providing a rapid overview of the product. 6.
Databases The diagram below illustrates the interoperation between the Access Server Driver and other components. Microsoft TCP/IP AVM Access Server Access Server Driver Network adapter (NDIS) Interoperation between the Access Server Driver and other components As an intermediate driver, the “AVM Access Server Driver” is able to control all communication between the network adapter and the operating system’s Layer 3 protocol stack.
User Interface User Interface Windows user interface (gui.exe) This is the main user interface to the AVM Access Server. This Windows application provides convenient, wizard-driven configuration of all AVM Access Server settings. Web user interface (AVM Webserver) This user interface is accessible through any browser with Javascript 1.2 capability (such as MS Internet Explorer Version 4.0 or later).
Installation Alongside AVM KEN! or AVM KEN! DSL Dynamic DNS, to remain accessible from the Internet at a fixed domain name using a dynamically assigned IP address. Direct support for dynamic DNS providers (currently implemented for the providers http://www.dyndns.org and http://www.dns4biz.com). Support for unmetered access: The connection is kept active as long as the service is running, rather than on demand. The connection is reestablished immediately after an interruption by the service provider.
Internet Access Through a Third-party Router services (such as HTTP, FTP) using the proxy server in KEN!, then you must activate appropriate IP packet filters in the Access Server to prohibit direct routing between the LAN and the Internet. Internet Access Through a Third-party Router The Access Server can also use an Internet connection through an existing router in the LAN.
IP Address Assignment: Static or Dynamic? IP Address Assignment: Static or Dynamic? The AVM Access Server defines two kinds of address ranges: those for static and those for dynamic address assignments. With dynamic IP address ranges, the user is only assigned an IP address when the connection is activated, and the address may be a different one each time the connection is dialed up.
IP Addresses From a Dedicated Subnetwork IP Addresses From a Dedicated Subnetwork Example: AVM Access Server: 172.16.1.1 Local network: 172.16.0.0 / 16 (172.16.0.1 to 172.16.255.254) IP address range for assignment to remote users: 192.168.20.0 / 24 (192.168.20.1 to 192.168.20.254) In this case, all computers in the LAN must have a route to the network 192.168.20.0/24.
Remote Network Connections 6.4 Remote Network Connections The AVM Access Server allows you to connect entire remote LANs to the local network. The Access Server provides the following features for remote network connections: IP routing direct ISDN connections (with up to 30 bundled B channels) VPN connections over the Internet NetBIOS spoofing As for remote user connections, the two locations can use IP addresses in the same subnetwork. In this case, the Access Server performs proxy ARP.
VPN and the IPsec Protocol Global forwarding filter Accept Decrypted data Global input filter Upper outgoing filter profile Upper incoming filter profile Global output filter Masquerading/NAT Masquerading/NAT IPSec Decryption IPSec Encryption Lower incoming filter profile Lower outgoing filter profile ISDN / ADSL / GSM / LAN ISDN / ADSL / GSM / LAN Accept Architecture of the filter profiles 6.
VPN and the IPsec Protocol The identities (IDs) exchanged in IKE Phase 1 can be: user fully qualified domain name (User FQDN) fully qualified domain name (FQDN) Key ID IP host address IP network address with subnet mask IP address range For remote users, the configured user name is accepted as User FQDN, FQDN and Key ID. For remote networks, all of the identity types listed above are configurable.
VPN and the IPsec Protocol IDs are used in Phase 2 as well. For remote users, the AVM Access Server’s identity is always the address of the uppermost access rule. For remote networks, the identities can be configured as desired. When the Phase 2 identity is set to “Automatic”, it is derived from the uppermost access rule. Security policies are proposed SAs. The security policies are named according to the structure described below.
Interoperability Hash algorithms: sha Secure Hash Algorithm 1 (SHA-1) md5 Message Digest 5 (MD5) all The SHA-1 and MD5 hash algorithms are proposed to the remote system in that order Compression techniques: lzjh LZJH (RFC 2395) deflate Deflate (RFC 2394) lzs LZS (RFC 3051) no Do not use payload compression Perfect forward secrecy: pfs Require perfect forward secrecy no-pfs Do not require perfect forward secrecy 6.
Interoperability PPP over ISDN RFC 1662 PPP in HDLC-like Framing RFC 1962 The PPP Compression Control Protocol (CCP) RFC 1968 PPP Encryption Control Protocol (ECP) RFC 1974 PPP Stac LZS Compression Protocol RFC 1989 PPP Link Quality Monitoring RFC 1990 The PPP Multilink Protocol (MP) RFC 1994 PPP Challenge Handshake Authentication Protocol (CHAP) RFC 2118 Microsoft Point-to-Point Compression (MPPC) Protocol RFC 2125 The PPP Bandwidth Allocation Protocol (BAP) / The PPP Bandwidth Allocation
Interoperability IPsec RFC 2408 Internet Security Association and Key Management Protocol (ISAKMP) RFC 2409 The Internet Key Exchange (IKE) RFC 2410 The NULL Encryption Algorithm and Its Use with IPsec RFC 2412 The OAKLEY Key Determination Protocol RFC 2451 The ESP CBC-Mode Cipher Algorithms RFC 2709 Security Model with Tunnel-mode IPsec for NAT Domains RFC 3051 IP Payload Compression Using ITU-T V.
Updates, Registration and Support 7 Updates, Registration and Support We’re always here to help you when you have questions or problems. Whether you need manuals, software updates, registration or support: all the service information you need is available. 7.
Internet Internet AVM also provides you with detailed information and free software updates over the Internet. Visit us at: www.avm.de/en/ Click “Products” for the latest information about all AVM products, as well as announcements of new products and product versions. Further Reading For information on the configuration of WAN-linked Microsoft networks, see: Active Directory Branch Office Planning Guide www.microsoft.com/windows2000/techinfo/planning /activedirectory/branchoffice/default.
AVM Data Call Center (ADC) You can also download software updates from AVM’s FTP server. Click the “FTP server” link in the download area, or see: www.avm.de/ftp AVM Data Call Center (ADC) The AVM Data Call Center (ADC) provides all of the same programs and drivers that are available from the AVM web site.
Support by E-mail 3. The Access Server has a built-in function to generate a file containing all the information about your configuration that may be relevant to your support request. – In the “Configuration” View of the AVM Access Server, select the “Administration” folder and open the “Service and Support” dialog page. – In the “Support data” area, click the “Generate Support Data...” button. The support data is saved in the file SUPPORT.ZIP in the Access Server installation folder.
Support by Fax Your fax should contain the following information: An e-mail address or fax number where you can be reached. Your name and address. The Product Identification Code, found on your CD. The AVM Access Server version you are using. The version number can be found in the Readme file. The number of the Microsoft Service Pack installed. The operating system used on the computer on which you have installed the AVM Access Server (Windows XP, 2000 or NT). The network protocols you are using.
Glossary ADSL (Asymmetric Digital Subscriber Line) ADSL is a communication technology that permits Internet access with high bandwidth over ordinary telephone cables. Data communication takes place at up to 6 Mbit/s downstream (that is, from the Internet to the user) and up to 640 kbit/s upstream. Other telecommunication services and dial-up connections to other subscribers are not possible over ADSL. ISDN and ADSL can be carried over the same telephone cable using different frequency bands.
Authentication Authentication refers to identifying a remote system by verifying its login information (name and password) on establishing incoming and outgoing connections. In the AVM Access Server, authentication is performed not only to prevent unauthorized access, but also to identify the remote user if incoming call assignment by CLI number is not activated. The authentication protocols used for PPP connections are PAP and CHAP.
Charge profile A charge profile contains information about the duration of a connection charge interval for each time of day and for local and long-distance dialing zones. Each profile consists of two lists of charge rates over a 24 hour period: one list applies on weekdays (Monday–Friday), the other on weekends and (optionally) holidays. The AVM Access Server uses charge profiles to control the inactivity timeout for the physical ISDN connection.
BRI lines and 64 kbit/s for PRI lines. D channel information is used for ISDN features such as charge information (AOCD) and caller ID (CLIP). In Germany, the CLIP and AOCD services must be specially requested on ordering an ISDN line. DNS (Domain Name System) DNS is the address resolution service in IP networks such as the Internet, providing other systems with a mapping between human-readable names and IP addresses. In other words, the DNS converts computers’ domain names into numeric addresses.
Domain controller In Windows networks, servers that are to share user account information can be grouped together in one or more domains. One server in the domain, the Domain controller or DC, stores all account information. The advantage of organizing servers in domains is that users can access all resources with a single user name and password. User account maintenance is simplified because all changes are entered only on the domain controller. DSS1 Standard European ISDN D-channel protocol.
Packet types that are constantly exchanged by certain applications in networks, and that would otherwise cause frequent unnecessary calls in an ISDN WAN, can be filtered out. Packet types whose destination address is in a subnetwork of the LAN that should not be accessible from outside can be filtered out. A filter profile consists of one or more filter rules and a default action. Each filter rule contains several conditions and an action.
otherwise prohibited by IP masquerading. A forwarding profile consists of a set of forwarding rules. These forwarding rules determine which IP packets are forwarded to which servers in the local-area network. The AVM Access Server always uses IP masquerading on Internet connections. If you want to allow access from the Internet to specific servers in your LAN, you must use a forwarding profile. See also “NAT (Network Address Translation)” on page 131.
HDLC (High-level Data Link Control) A communications protocol standardized by ISO for data packets over serial lines. HDLC is actually a structured set of standards which define the means by which dissimilar devices can communicate over data networks. HDLC is a bit-oriented and hence code-independent data link protocol for point-to-point and point-to-multipoint connections. HDLC is also standardized by ITU-T (ITU = International Telecommunication Union; ITU-T = ITU Telecommunication Standardization Sector).
IP (Internet Protocol) IP is the Network Layer protocol responsible for addressing and routing in the TCP/IP protocol family. In general terms, its purpose is to provide data communication between various networks. IP provides: data packet transmission fragmentation of data selection of communication parameters addressing routing between networks identification of higher-order protocols IP does not provide assured transmission: the sender receives no verification that the packet was delivered.
Every IP address contains two components: the network address and the host address. The sizes of the network address and the host address are variable, and determined by the first four bits (of the first byte) of the IP address. Class A addresses consist of a one-byte network address and a three-byte host address: X._._._ Network address Host address Class A addresses Example: 88.120.5.120 (88 is the network address, 120.5.120 is the host address).
RFC 1918 (Address Allocation for Private Internets) reserves the following parts of the IP address space for use in private networks: 10.0.0.0 – 10.255.255.255 (the 10/8 prefix) 172.16.0.0 – 172.31.255.255 (the 172.16/12 prefix) 192.168.0.0 – 192.168.255.255 (the 192.168/16 prefix) IP mask: see “Subnet mask” on page 135 IP masquerading Also known as Network Address Translation, or NAT.
LAN (Local-Area Network) A computer network limited to a given location, such as a company site or a government agency’s office building. Remote computers can use appropriate software (such as the AVM Access Server) to join a LAN over ISDN, ADSL, GSM or VPN connections. Logical ISDN connection A logical ISDN connection refers to the situation in which two computers consider an ISDN connection between them, which can be dialed up in one or two seconds, to be virtually continuous.
NAT (Network Address Translation) NAT is a technique in which a router replaces addresses and port numbers in IP, UDP and TCP packet headers with other values. The AVM Access Server performs NAT using a table to map the original IP address and port numbers to new values. For incoming connections handled by a forwarding profile, this table is static. Outgoing connections are handled dynamically by IP masquerading. IP masquerading and forwarding profiles are special uses of NAT.
PAP (Password Authentication Protocol) One of the two authentication protocols in the PPP suite. A name and password for the remote system must be configured on the system that requests authentication. The remote system must be configured to present the same name and password. In PAP authentication, the name and password are sent unencrypted, and the authenticating system simply compares them with its settings. If they match, the remote system is authentic and the connection can be set up.
“Well-known ports” are destination port numbers that are reserved for common network services and applications by IANA, the Internet Assigned Numbers Authority. Well-known ports are in the range from 1 to 1023. PPP over ISDN (Point-to-Point Protocol) A communication protocol for circuit-switched networks such as ISDN that provide protocol-independent communication on ISO OSI Layer 2. PPP over ISDN incorporates a collection of subordinate standards and protocols.
router becoming unavailable, for example), it forwards this information to the surrounding routers. Furthermore, a RIP router sends broadcasts at regular intervals to publish its entire database of routing information. These broadcasts ensure that all routers in the internetwork are synchronized. Route A route is the path traveled by a data packet through the network from its source to its destination. A return route is also necessary in order for the receiver to send a response.
The responses are therefore “spoofed”, or generated at the local end using the remote client’s source address. If the ISDN connection is physically active, the packets can be sent over the ISDN line. As soon as the physical connection is interrupted by the inactivity timeout, and as long as the logical ISDN connection persists, the remote access software answers the packets locally, simulating the existence of a physical connection to the remote site.
subnet mask (255.255.255.0) as a quasi-Class C address. An individual IP host address can also be considered as a network address with a 32bit subnet mask. The table below shows the number of host addresses in a subnetwork for subnet masks used by the Access Server. Host addresses Addresses in subnet Mask (one-bits) Mask (dotteddecimal) 000-255 256 24 255.255.255.0 000-127 128-255 128 25 255.255.255.128 000-063 064-127 128-191 192-255 64 26 255.255.255.
Host addresses Addresses in subnet Mask (one-bits) Mask (dotteddecimal) 000-007 008-015 016-023 024-031 032-039 040-047 048-055 056-063 064-071 072-079 080-087 088-095 096-103 104-111 112-119 120-127 128-135 136-143 144-151 152-159 160-167 168-175 176-183 184-191 192-199 200-207 208-215 216-223 224-231 232-239 240-247 248-255 8 29 255.255.255.248 Subnet masks in the AVM Access Server TCP (Transmission Control Protocol) TCP is a connection-oriented protocol for use over packet-oriented networks.
TCP/IP address: see “IP address” on page 127 Tunneling Tunneling is a technique in which the packets of a given protocol are transparently transported in those of another protocol. The resulting transparent connection between the endpoints of the transport is called a tunnel. The data packets of the transported protocol are encapsulated for transport in those of the second protocol. At the other end of the tunnel, the encapsulated packets are extracted again.
Index A F active IP routes 39 ADSL 8 AVM Access Server uses 7 AVM Support 114 AVM support sources of information 114 support by e-mail 117 support by fax 117 filters 58 destination-specific input filters 59 destination-specific output filters 59 firewall 58 forwarding filter 59 global input filter 59 global output filter 59 IP filter profiles 62 IP filters 58 firewall 58 forwarding profiles 75 B B-channel reservations 78 C CAPI 2.
M S menus 31 monitoring functions 36 events 40 ISDN B channels 39 packet trace 43 routing table 39 use statistics 40 monitoring view 36 monitoring: see monitoring functions MSN: see multiple subscriber number Multiple Subscriber Number 13 schedules 79 static routing 78 statistics functions status 37 support 114 T toolbar 33 transport protocols tunnel 81, 82 87 U N negotiation 89 network protocols Ntr.mdb 43 Ntrlog.