User manual
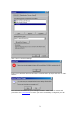
For 64bits encryption, 10 hexadecimal
3
values must be presented in the key field.
While 128 bits encryption, 26 hexadecimal values must be in the key field.
Authentication Type
Share Key: Encryption algorithm used on each of the computers or access points
might different. Hosts must discover which algorithm other remote hosts use
before proper communication could be established.
Open System: The IEEE 802.11 default authentication method, which is a very
simple, two-step process. First the station wanting to authenticate with another
station sends an authentication management frame containing the sending
station’s identity. The receiving station then sends back a frame alerting whether it
recognizes the identity of the authenticating station.
WEP standard did not specify which algorithm or the procedure to be used. In
practice, most installation uses a single algorithm that is shared between all mobile
stations and access points.
How is encryption key generated?
Firstly, 24bits IV is generated. This IV is then pass through an encryption
algorithm generator with your data. The generator will generate the appropriate
length of bits that represents your encrypt data.
3
Hexadecimal numbers range from 0 ~ 9 and A ~ F.
80