Owners manual
KVM Access Management Software User Manual122
LDAP Group Authorization Setting Examples
Example 1. In this example the external server is OpenLDAP on Windows Server 2003 as shown in the
“LDAP/LDAPS - OpenLDAP Setting Example” on page 118.
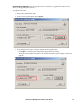
1. Under the KVM ACCESS User Manager tab, select Authentication Services > Authentication
Servers.
2. Select the OpenLDAP server, then click Group Authorization.
3. Click the Group has Member attribute radio button.
4. Click Add (at the top-right of the panel).
5. In this example add the groups1 group.
The OpenLDAP administrator uses this name (groups1 in the example) to create a group under
OpenLDAP with the same name as the one just created on the KVM ACCESS server, as follows:
1. Open the core.schema file. The default settings we are interested in are as follows:
attributetype ( 2.5.4.31 NAME 'member'
DESC 'RFC2256: member of a group'
SUP distinguishedName )
objectclass ( 2.5.6.9 NAME 'groupOfNames'
DESC 'RFC2256: a group of names (DNs)'
SUP top STRUCTURAL
MUST ( member $ cn )
MAY ( businessCategory $ seeAlso $ owner $ ou $ o $ description ) )
2. Edit the kvmaccessldap.ldif file to add a definition for groups1 and have KVM ACCESS user
accounts fall under groups1, as follows:
dn: cn=groups1,ou=groups,dc=apc,dc=com
objectclass: groupofnames
member: cn=kvmaccess,ou=software,dc=apc,dc=com
cn: groups1
Note:1. The entry after dn: cn= should be the name of an actual group created under
Group Authorization (see Group Authorization, page 72) on the KVM ACCESS
server.
2. The entry after objectclass: should be consistent with the name that was entered for
the Object class when the group was created on the KVM ACCESS server. Change
the default entry in this file to match.
3. The entry after member: cn= should be an actual user login name.
3. You can check the group definition with LDAP Browser.
4. The above example has added a member, kvmaccess, to the groups1 group. To add additional
members to the group, edit the file to include them. For example:
member: cn=kvmaccess-1,ou=software,dc=apc,dc=com
member: cn=kvmaccess-2,ou=software,dc=apc,dc=com
Once these procedures are completed, KVM ACCESS users who are authenticated through the LDAP/
LDAPS server, are authorized according to the permissions assigned to the group.