Wireless Touch Panel with Intercom Reference Guide
Table Of Contents
- MVP-8400iModero® ViewPoint® Wireless Touch Panel with Intercom
- MVP-8400i Modero Viewpoint Wireless Touch Panel With Intercom
- MVP-BP Power Pack
- NXA-CFSP Compact Flash
- Wireless Interface Cards
- Configuring Communications
- Modero Setup and System Settings
- Wireless Settings Page - Wireless Access Overview
- Configuring a Wireless Network Access
- Step 1: Configure the Panel’s Wireless IP Settings
- Step 2: Configure the Card’s Wireless Security Settings
- Step 3: Choose a Master Connection Mode
- Using G4 Web Control to Interact with a G4 Panel
- Using your NetLinx Master to control the G4 panel
- Upgrading MVP Firmware
- Setup Pages
- Navigation Buttons
- Setup Pages
- Information
- Protected Setup Pages
- Protected Setup Navigation Buttons
- G4 Web Control Page
- Calibration Page
- Wireless Settings Page
- Wireless Security Page
- Open (Clear Text) Settings
- Static WEP Settings
- WPA-PSK Settings
- EAP-LEAP Settings
- EAP-FAST Settings
- EAP-PEAP Settings
- EAP-TTLS Settings
- EAP-TLS Settings
- Client certificate configuration
- System Settings Page
- Other Settings
- Tools
- Programming
- Panel Calibration
- Appendix A: Text Formatting
- Appendix B - Wireless Technology
- Appendix C: Troubleshooting
- Checking AMX USBLAN device connections via Windows Device Manager
- Checking AMX USBLAN device connections via NetLinx Studio
- USB Driver
- Panel Not in Listed As a Connected Device
- Connection Status
- Panel Doesn’t Respond To Touches
- Batteries Will Not Hold Or Take A Charge
- Modero Panel Isn’t Appearing In The Online Tree Tab
- MVP Can’t Obtain a DHCP Address
- My WEP Doesn’t Seem To Be Working
- NetLinx Studio Only Detects One Of My Connected Masters
- Can’t Connect To a NetLinx Master
- Only One Modero Panel In My System Shows Up
- Panel Behaves Strangely After Downloading A Panel File Or Firmware
- Panel Fails to Charge in MVP-WDS
Setup Pages
82
MVP-8400i Modero Viewpoint Wireless Touch Panels
Refer to the Using the Site Survey tool section on page 22 for more information on using this
feature.
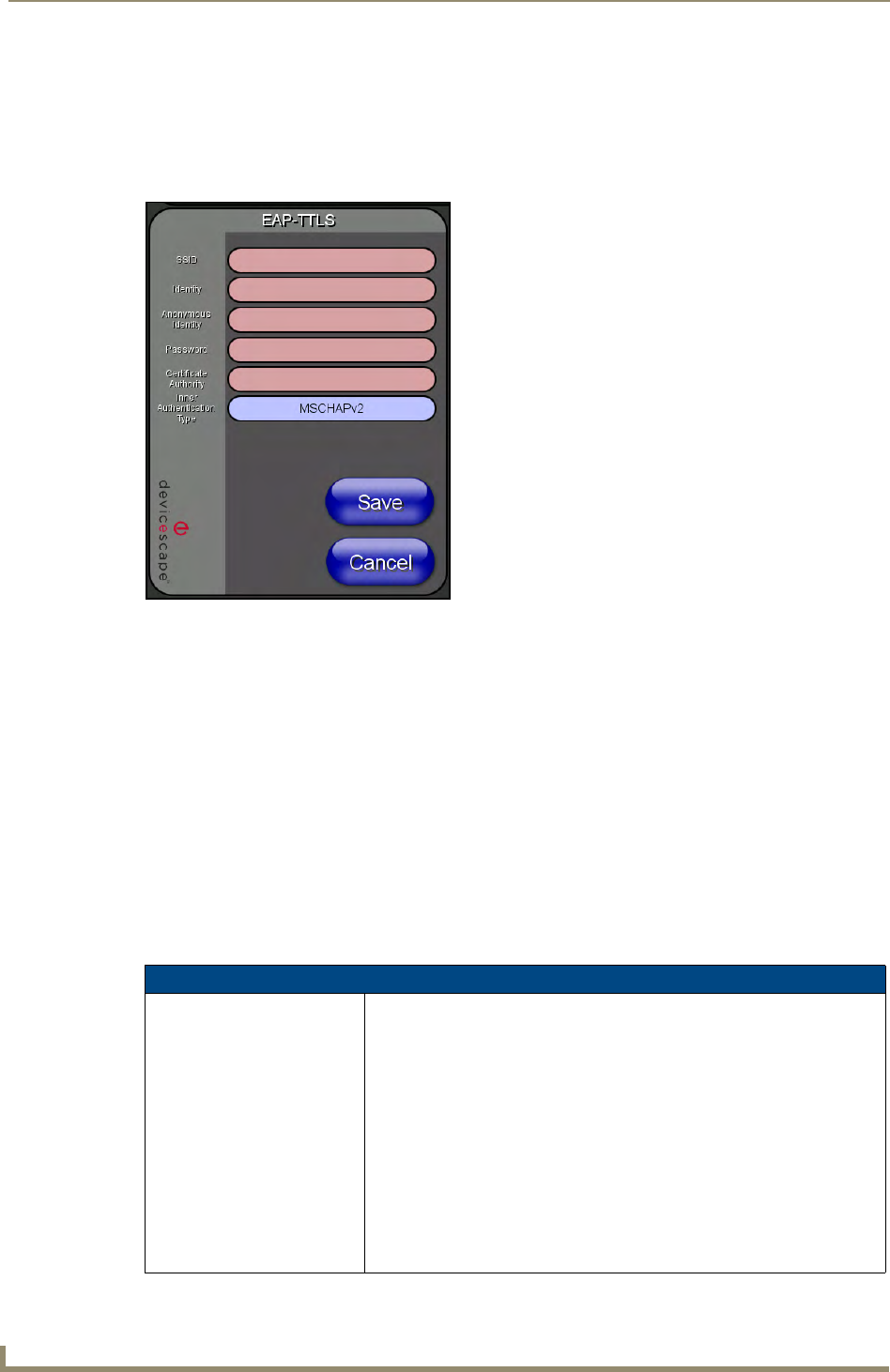
EAP-TTLS Settings
Press the EAP-TTLS button to opens the EAP-TTLS Settings page (FIG. 64).
TTLS (EAP Tunneled Transport Layer Security) is an authentication method that does not use a client
certificate to authenticate the panel. However. this method is more secure than PEAP because it does not
broadcast the identity of the user. Setup is similar to PEAP, but differs in the following areas:
An anonymous identity must be specified until the secure tunnel between the panel and the
Radius server is setup to transfer the real identity of the user.
There is no end-user ability to select from the different types of PEAP.
Additional Inner Authentication choices are available to the end-user.
EAP-TTLS security is designed for wireless environments where it is necessary to have the Radius
server directly validate the identity of the client (panel) before allowing it access to the network. This
validation is done by tunneling a connection through the WAP and directly between the panel and the
Radius server. Once the client is identified and then validated, the Radius server disconnects the tunnel
and allows the panel to access the network directly via the target WAP.
FIG. 64 Wireless Settings page - EAP-TTLS Settings
EAP-TTLS Settings
SSID (Service Set Identifier): Opens an on-screen keyboard to enter the SSID name used on the target
WAP.
The SSID is a unique name used by the WAP, and is assigned to all panels
on that network. An SSID is required by the WAP before the panel is
permitted to join the network.
• The SSID is case sensitive and must not exceed 32 characters.
• Make sure this setting is the same for all points in your wireless network.
• NXA-WAP200Gs use AMX as their default SSID.
• With EAP security, the SSID of the WAP must be entered. If it is left blank,
the panel will try to connect to the first access point detected that supports
EAP. However, a successful connection is not guaranteed because the
detected WAP may be connected to a RADIUS server, which may not
support this EAP type and/or have the proper user identities configured.










