User guide
Table Of Contents
- AWS SDK for .NET
- Table of Contents
- AWS SDK for .NET Developer Guide
- Getting Started with the AWS SDK for .NET
- Programming with the AWS SDK for .NET
- AWS SDK for .NET Tutorials and Examples
- Managing ASP.NET Session State with Amazon DynamoDB
- Tutorial: Creating Amazon EC2 Instances with the AWS SDK for .NET
- Tutorial: Grant Access Using an IAM Role and the AWS SDK for .NET
- Tutorial: Amazon EC2 Spot Instances
- Creating and Using an Amazon SQS Queue with the AWS SDK for .NET
- Creating an Amazon Route 53 Hosted Zone and Adding Resource Record Sets
- Additional Resources
- Document History
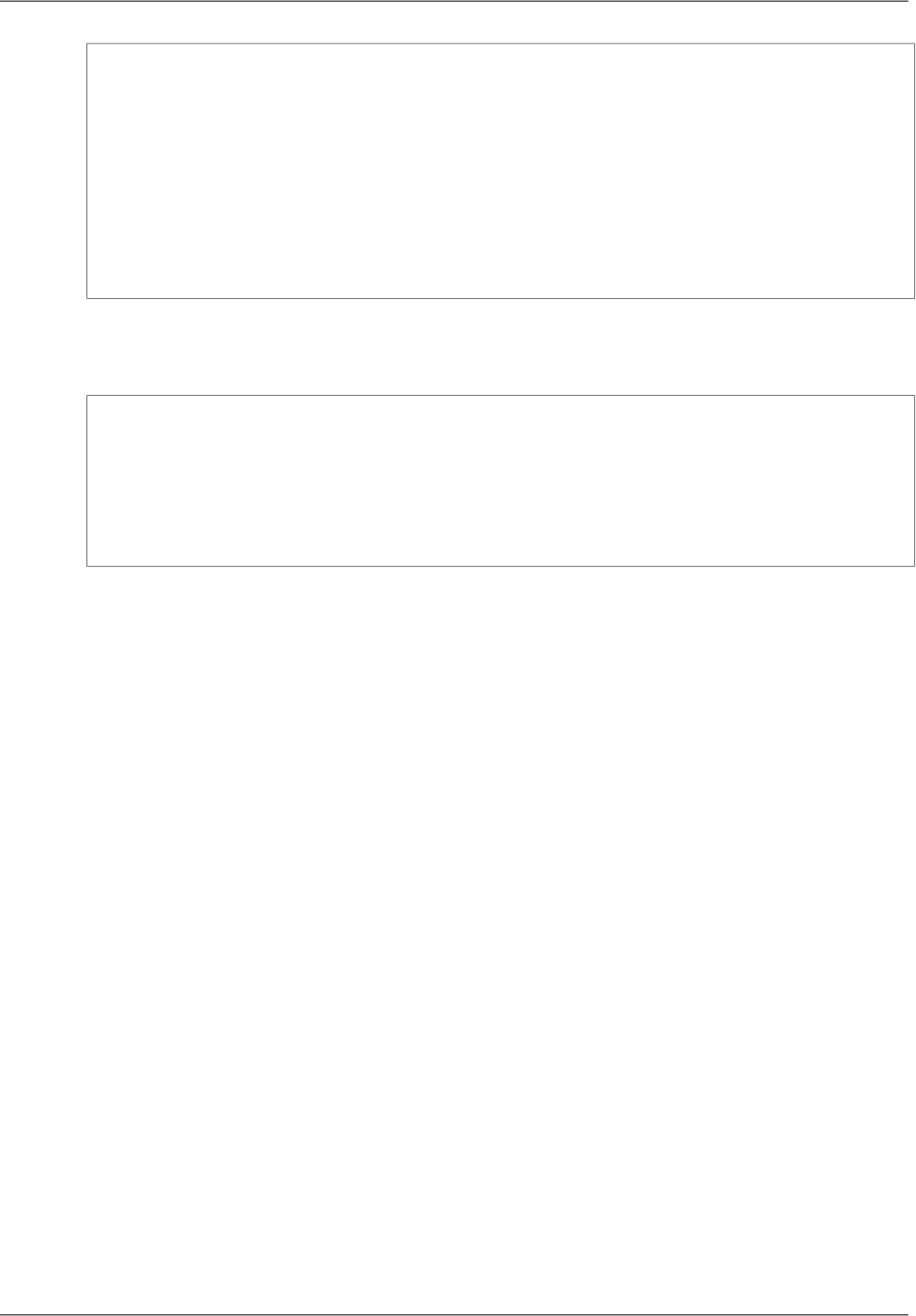
var deleteRequest = new TerminateInstancesRequest()
{
InstanceIds = instanceIds
};
var deleteResponse = ec2Client.TerminateInstances(deleteRequest);
foreach (InstanceStateChange item in deleteResponse.TerminatingInstances)
{
Console.WriteLine();
Console.WriteLine("Terminated instance: " + item.InstanceId);
Console.WriteLine("Instance state: " + item.CurrentState.Name);
}
To list the terminated instances
You can use the response object as follows to list the terminated instances.
List<InstanceStateChange> terminatedInstances = termResponse.TerminateInstances
Result.TerminatingInstance;
foreach(InstanceStateChange item in terminatedInstances)
{
Console.WriteLine("Terminated Instance: " + item.InstanceId);
}
Tutorial: Grant Access Using an IAM Role and
the AWS SDK for .NET
All requests to AWS must be cryptographically signed using credentials issued by AWS. Therefore, you
need a strategy for managing credentials for software that runs on Amazon EC2 instances.You must
distribute, store, and rotate these credentials in a way that keeps them secure but also accessible to the
software.
We designed IAM roles so that you can effectively manage AWS credentials for software running on EC2
instances.You create an IAM role and configure it with the permissions that the software requires. For
more information about the benefits of this approach, see IAM Roles for Amazon EC2 in the Amazon
Elastic Compute Cloud User Guide for Microsoft Windows and Roles (Delegation and Federation) in
Using IAM.
To use the permissions, the software constructs a client object for the AWS service.The constructor
searches the credentials provider chain for credentials. For .NET, the credentials provider chain is as
follows:
• The App.config file
• The instance metadata associated with the IAM role for the EC2 instance
If the client does not find credentials in App.config, it retrieves temporary credentials that have the
same permissions as those associated with the IAM role. The credentials are retrieved from instance
metadata.The credentials are stored by the constructor on behalf of the customer software and are used
to make calls to AWS from that client object. Although the credentials are temporary and eventually expire,
the SDK client periodically refreshes them so that they continue to enable access. This periodic refresh
is completely transparent to the application software.
Version v2.0.0
47
AWS SDK for .NET Developer Guide
Tutorial: Using an IAM Role










