User Guide
Configuring Virtual Private Networks 151
Chapter 12
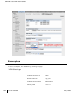
1. Set the type of
IKE Hash Algorithm, SHA or MD5 in the IKE Policies page.
2 In case Pre-shared was selected as the IKE Authentication in the IKE Poli-
cies page (as described in the L2TP IPSec configuration), key in the
pre-share key used in the L2TP configuration. NOTE: The two keys should
match.
3 Select the Group configuration as per the IKE Policy configuration setting
for
Diffie Helman Group.
4 Select the IPSEC Encryption as per the IKE Policy configuration setting for
Encryption.
5 Select the IPSEC Hash Algorithm as per the
Algorithm selected on the IKE
Policy page of IPSEC.
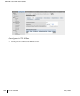
6Click
Apply to apply the changes made prior to navigating to another
page.
7 The VPN dialer can be downloaded using Captive Portal. To enable this, in
the role the user gets assigned after captive portal, configure the dialer by
the name used to identify the dialer.
Example if my captive portal user gets the guest role after logging on through
captive portal and my dialer is called mydialer, configure mydialer as the dialer
to be used in the guest role.