User's Manual Part 2
錯誤! 尚未定義樣式。
Wireless Networking Gateway System Manual
3-43
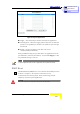
Figure 38: Special Applications
Trigger – The outbound port number issued by the application.
Incoming Ports – When the trigger packet is detected, the inbound
packets to the specified port numbers are allowed to pass through
the firewall.
Enable – Check to enable the rule. Each rule can be
enabled/disabled individually.
Some predefined settings are provided. Select an application from the
pre-defined list, select the ID number (1-10) and click Copy to, to add
the predefined setting to your list.
NOTE
If Special Applications fails to make an application work, try DMZ host instead.
DMZ Host
Demilitarized Zone (DMZ) Host is a host without the firewall protection.
It allows a computer to be exposed to unrestricted 2-way
communication for Internet games, Video conferencing, Internet
telephony, and other special applications.
CAUTION
This feature exposes your computer and may cause security issues.
刪除: Set TCP/IP Protocol
for Working with NAT
Router
刪除: Wizard