User guide
getting
started
welcome
rter
inormation
41
te
manager
te
connector
Appendix 2 - What are S3 connections?
ADDER.NET allows an alternative mechanism, called S3, to
be used for authenticating to devices. Using S3, ADDER.NET
contacts the device to inform it directly that the connection is
authorised and then passes matching credentials to the client’s
VNC viewer. The credentials time-out after a few seconds. This
has the following advantages:
• Unliketickets,which(ifthedevice’sclockcanbesetinto
the past) can be re-used by an attacker, stale credentials can
never be used.
• Wherethereareclocksynchronisationproblems,devicescan
become inaccessible with all tickets being reported as out
of date. As this method is independent of clock setting, it is
immune to problems of this type.
However using S3 does require all firmware and software to be
up-to-date. All of the following are necessary:-
• ADDER.NET1.7orlatermustbeused.
• ThedevicesmusthavermwarethatsupportsS3,aslisted
below:
S3 support within Adder units
Device type First S3 version
AdderLink IP Gold v2.1
AdderView CATxIP 5000 v1.11
Notes:
It is recommended that S3 is always used when managing
the above devices.
Connections can still be made with other devices, however,
tickets will always be used in place of S3.
• ClientPCsmusthaveADDER.NETv1.7orlaterVNC-URI
Clientsoftware.TheADDER.NETv1.6(andearlier)VNC-URI
Client software will not work. It typically connects to the
device but without authentication so the user is prompted
for a password.
• ThecongurationparameterUse S3 within ADDER.NET
must be switched on. This is disabled by default due to an
incompatibilitywithv1.6client-sidesoftware.
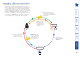
Host
PC
KVM-over-IP
eviced
ADDER.NET
User
1
2
3
4
5
6
Access
Log
Host
PC
S3
credentials
S3
credentials
1 The user’s VNC
Viewer requests
access to a
specific host
computer.
3 ADDER.NET sends
S3 credentials back
to the user giving
timed access to the
host computer.
4 User’s VNC viewer uses
the ticket to automatically
authenticate to the KVM-
over-IP appliance.
5 A VNC session is
established that
provides access to
the requested host
computer.
6 All activities are
fully logged within
ADDER.NET
2 Connection
authorisation is
sent directly to
the device.